Application security is an afterthought. Unsecure applications are one of the major causes for cyberattacks. It has been observed that 40% cyber-attacks are initiated through the web application penetration. These attacks can be avoided if the web applications are cyber secure.
Not only the vulnerable code developed by the developers but also many vulnerabilities in the underlying platform can cause of the attack. For example, vulnerabilities in web server, application server, operating system, third party APIs and even the web browser clients contribute to the web application vulnerabilities. Though developers don’t have control over these vulnerabilities, they can play their part and make sure that their own code is secure.
It is a general practice to perform the security assessment of the web application before Go Live. The production roll out can be delayed due to the severe vulnerabilities in the web application. The efforts required to rework on these security gaps at rollout stage and its impact are very high.
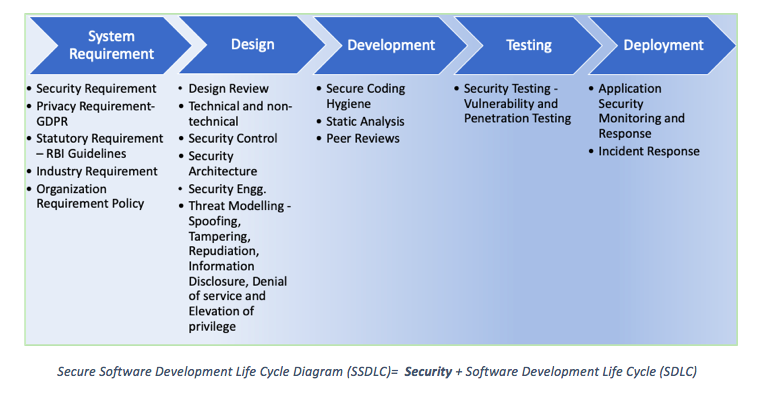
The security aspect of the application should be considered from the Day 1 of the Project initiation. As recommended by experts, security needs to be shifted to the leftmost phase, the Requirement Analysis of the Software Development Life Cycle (SDLC) and should be considered at every phase of the SDLC. This new SDLC is called Secure Software Development Life Cycle (SSDLC). It is a time for IT firms to move from SDLC to SSDLC.
Following are the few key changes that need to be carried out by Organizations to move to SSDLC :
– Need to change the Standard Operating Procedures for Software Engineering and add substages or tasks to gather and implement the security during the Project Development and Maintenance Life cycle
– Templates need to undergo changes so that the security information will be captured and implemented during project development as described below.
· The Requirement Gathering template should be modified to gather and analyze the security requirement of the project, especially for the confidential/sensitive data, regulatory compliances, etc.
· The Design template should capture the requirement of the security controls , access controls, encryption, etc.
· Secure coding practices check list.
· Invest in good Static Application Security Testing (SAST) automated tool
· Security Test Plan in addition to the Unit test plan to perform the security testing
– As recommended by AppSec, each project team should have a security champion to take the ownership and guide the rest of the project team on web application security.
Secure Software Development Life Cycle Diagram (SSDLC)= Security+ Software Development Life Cycle (SDLC)
Developer plays an important role in developing secure applications. They should strive to build security into every application they develop. It is mandatory for IT firms to educate developers on web application security. Building the security into the system is much easier than adding into the existing system.
Here are few areas of development that Developers needs to take care while coding as suggested by OWASP-
– Sanitizing all your Inputs, not only at the client site but also at server site if required.
– For Authentication, use password strength control and Multifactor authentication
– Use Role Based Access Controls.
– Use parameterized SQL commands for all data access
– Do not disclose sensitive information in error responses including system details, session identifiers or account information.
– Always use HTTPS.
– Don’t use the default user accounts of Database or Application Server
– Avoid Insure Direct Object Response to the internal implemented object like database record.
– Use custom headers only on a specific site or application and not at server level
– Update the HTTP Headers for following parameters:
· HTTP Strict Transport Security (HSTS) helps against cookie hijacking
· X-Frame-Options help to block the clickjacking
· X-Content-Type-Options prevent MIME-sniffing attacks
· Content-Security-Policy to frame the content by the current site only and whitelist specific sources and endpoints
· X-Permitted-Cross-Domain-Policies
· X-XSS-Protection helps to protect against cross site scripting
· Disable caching for confidential information using the Cache-Control header.
DigiSec360 is helping organizations to implement Secure Software Development Life Cycle (SSDLC) and offer application security assessment solutions.
Connect to us [email protected] for more details.