Organizations across industries are moving their data to the Cloud. The oblivious reasons for this mass adoption are cost benefits and scalability. But What about the Security? Are your data and applications secure on Cloud?
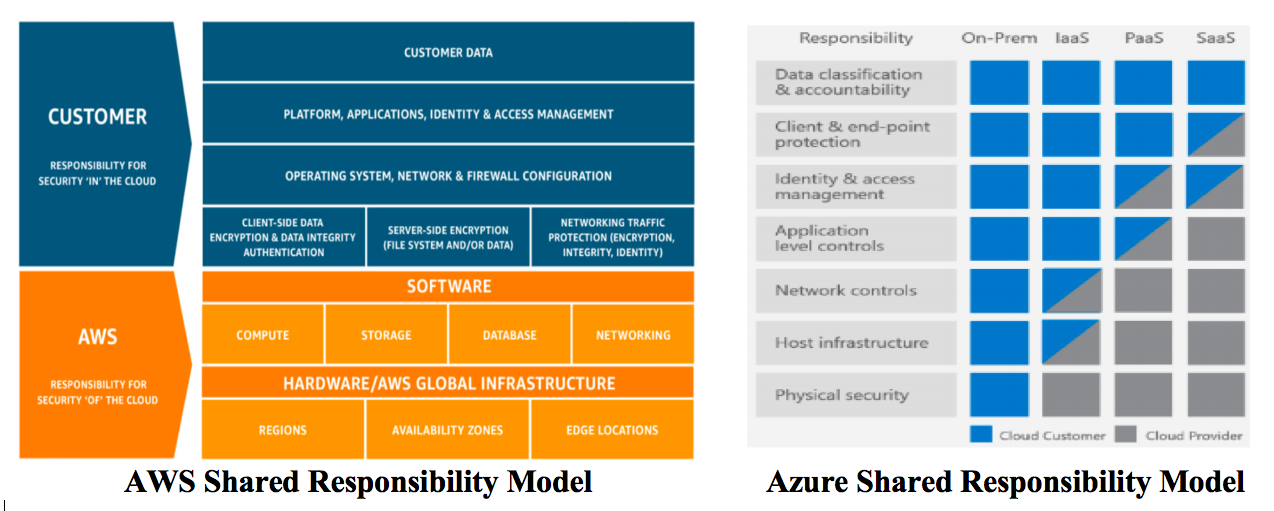
Cloud Security is the shared responsibility of both Cloud Service Providers (CSP) and Cloud Consumers. The shared responsibility model is divided into two parts, Security of the Cloudand Security in the cloud.
The CSP is responsible for the Security of the Cloud while Cloud Consumers are responsible for Security in the Cloud. The CSP is responsible for the infrastructure security that runs the Cloud Services. It includes hardware, software, networking and facilities that run the cloud services.
You are responsible for the security of your data and applications stored in the Cloudand your responsibility changes based on the cloud deployment types like IaaS, PaaS, SaaS and on-premise. To ensure the Cloud Security, you need to have
– A complete visibility of your cloud resources to check their security posture and take appropriate action on potential areas of weakness.
– Data Classification based on its sensitivity
– Configuration & Management of the security controls
The market CSP leaders, AWS and Azures has published their Shared responsibility Model as shown below. It clearly dictates the security responsibilities between CSP and the cloud customers.
While performing the web application pen testing and Cloud Security audit, we observed that misconfiguration of the cloud is one of the leading causes for the vulnerabilities.
Here are the few tips to improve your Security in Cloud :-
– Logging and Monitoring
Your Security starts from the logging and monitoring task. There are cloud services for automatically logging all important events like console and API calls e.g., AWS CloudTrail, Amazon S3 Assess Log, Azure Activity Logs etc. You need to encrypt these log files and implement proper access controls for it. The unauthorized access and deletion of these log files should be restricted.
After maintaining the logs, the next step is periodically assessing it to get the comprehensive view of your security posture.
– Identity and Access Management (IAM) Validations
Identity and Access Management help you to define security controls for all your Cloud resources. You can create Users, Roles, Groups and Polices for identification, Authentication and Authorization. You need to regularly revalidate the existing Users, Roles and Policies and remove the unwanted access. If you are using the access keys, make sure that it is updated and rotated frequently.
– Use Multi Factor Authentication (MFA)
MFA provides an extra security layer in Authentication process. You need to enable it not only to the root user but also for other IAM users to protect your Cloud resources.
– Encryption
The CSP provides encryption to protect your data in Rest and also in Transit. You can use multiple options for encryption like client site encryption, server site encryption. You can either use default encryption or go for custom encryption solution. It is good practice to use different keys for encryption and decryption.
– Implement Security Best Practices suggested by CSP
You should implement the Security Best Practices suggested by the CSP. Microsoft and Amazon has provided good documentation on Best Practices for each Cloud service they are providing.
– Audit your cloud security using CIS Benchmark
Center for Internet Security (CIS) publishes the best practices for securing operating systems, software, cloud providers, mobile devices and network devices. You should verify your cloud security controls implementation against these Benchmarks. You will find the CIS benchmark for all leading CSPs like AWS, Microsoft, Google, IBM, etc.
At DigiSec360 our focus is on cybersecurity. We eliminate the majority of cybersecurity risks with data protection measures and regular security audits. DigiSec360 specialists can ensure high-end security of your cloud environments thanks to our experience working with the most robust cloud technologies. DigiSec360 experts continuously watch for new technology trends and expand their cloud security expertise.
With our assistance, you can leverage services for cloud management while keeping things easy and secure.