The future Internet, Web 3.0, is decentralized and built on blockchain technology. As a result, […]
Blog
How to protect your business from Cyberattacks
Assess your business risk The first step in improving your cybersecurity is understanding your risk […]
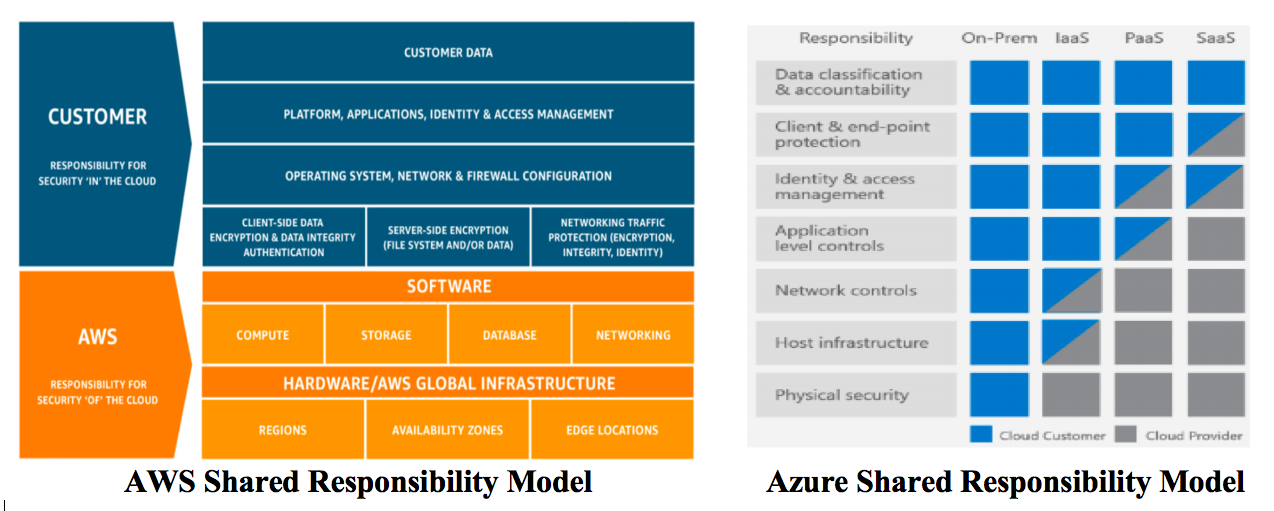
Cloud Security Control Considerations
Organizations across industries are moving their data to the Cloud. The oblivious reasons for this […]
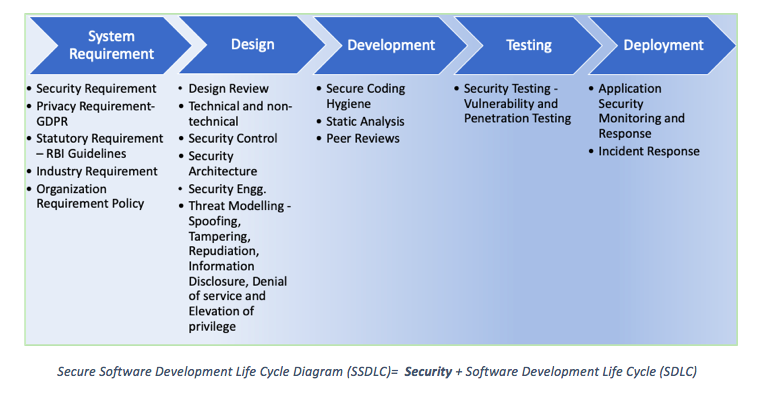
SSDLC : Secure Application Development
Application security is an afterthought. Unsecure applications are one of the major causes for cyberattacks. It […]
Preparing for Secure Work From Home culture
Measures being introduced to tackle the COVID-19 coronavirus mean that many organizations are having to […]